Tip 1. Minimize change to the Default Policies
Active Directory contains two default policies:
Default Domain Policy and Default Domain Controllers Policy.
Default Domain Policy
Applies settings at the domain level.
Affects all users and computers.
The Default Domain Policy should only set the following:
* Password Policy
* Domain Account Lockout Policy
* Domain Kerberos Policy
Default Domain Controllers Policy
Applies settings to the domain controllers OU.
Affects only Domain Controllers computers.
The Default Domain Controllers Policy should only set the following:
* User Rights Assignment Policy
* Audit Policy
GPOs linked at the root domain level will apply to all users and computers in the domain.
This could lead to apply to objects that you don’t want.
It’s better to apply the policies at a more specific level (OU level).
Tip 3. Organize your OU structure
A good OU structure makes it easier to manage and troubleshoot multiple group policies.
* Avoid mixing different types of Active Directory objects (like users and computers) in the same OU. Instead, separate users and computers in separated OUs.
{This will makes it easier to apply computer policies just to the computers and user policies only to the users}.
Tip 4. Link GPOs at the OU root level
With your OU structure in place, you can start linking GPOs. Link GPOs at the highest level allow child OUs to inherit the settings.
This method avoids linking the same GPO to multiple OUs.
User - Microsoft Office Settings GPO applies to all users in the organization.
Executives require a few custom settings GPO {should not apply to other departments}. Therefore, it linked to certain OUs (Human Resources &Sales), preventing the settings from applying to other users.
Tip 5. Avoid "Block inheritance" and "Enforced" options
Blocking GPO inheritance at the OU level prevents the application of higher-level policies, such as from a parent OU or the root domain.
Policy enforcement ensures that any later policy does not overwrite the GPO settings and configuration.
Using either of these methods can make troubleshooting confusing.
You may not be aware that a policy is blocked or a higher policy is being enforced.
**** Enforced overrides Block inheritance *****
If a policy is enforced at a higher level but later encounters an inheritance block, the enforced policy will win.
Tip 6. Group Policy Order of Precedence
GPOs linked to an organizational unit at the highest level in Active Directory are processed first, followed by GPOs that are linked to its child organizational unit, and so on.
This means GPOs that are linked directly to an OU that contains user or computer objects are processed last, hence has the highest precedence.
If you want to remove a GPO from an OU, delete the link instead of disabling the GPO.
Removing a link does not delete the GPO itself and only ensures the settings are no longer applied.
Tip 8. Be descriptive with GPO Names
Use descriptive names so you can quickly identify the GPO’s purpose.
This will help in troubleshooting.
Tip 9. Disable unused computer and user configurations
If a policy only contains computer or user settings, disable the other configuration settings.
This action can slightly decrease GPO processing time as the computer or user account does not need to worry about settings that do not apply.
Tip 10. Simplify administration with smaller GPOs
Avoid collecting every setting and configuration into a single, large GPO.
Smaller GPOs enable easier management and simplified design and implementation.
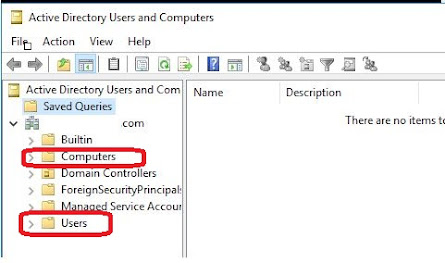
Tip 11. Avoid using the Users or Computers folders in Active Directory
Active Directory comes with default Users and Computers folders at the root domain level.
However, these folders are not OUs it is Containers, and you cannot link GPOs to.
Tip 12. Backup group policies
Group policies are a critical component of Active Directory infrastructure.
Therefore, you should perform regular backups of the policies as part of your disaster recovery plans.
Tip 13. Best Practices for Group Policy Performance
Here are some settings that can cause slow startup and logon times.
* Login scripts downloading large files
* Startup scripts downloading large files
* Mapping home drives that are far away
* Deploying huge printer drivers over group policy preferences
* Overuse of group policy filtering by AD group membership
* Using excessive WMI filters
* Lots and lots of GPOs linked to a user or computer over a slow link.
Tip 14. Use WMI filters sparingly
Windows Management Instrumentation (WMI) filters allow you to target GPOs based on computer or user attributes.
Attributes in WMI include the operation system version or OS architecture (32 or 64-bit).
Using too many WMI filters causes slowdowns at computer startup and user login, which leads to a bad user experience.
Instead of WMI filters, try to use GPO security filters instead.
Security filters control which users, groups, or computers that GPO settings apply. By default, any policy is scoped to Authenticated Users, which applies to any authenticated users in the OU.
Use RSop and gpresult commands used to verify and troubleshoot group policy.
When troubleshooting you need a way to verify that GPOs are getting applied and check exactly what policies are applied.
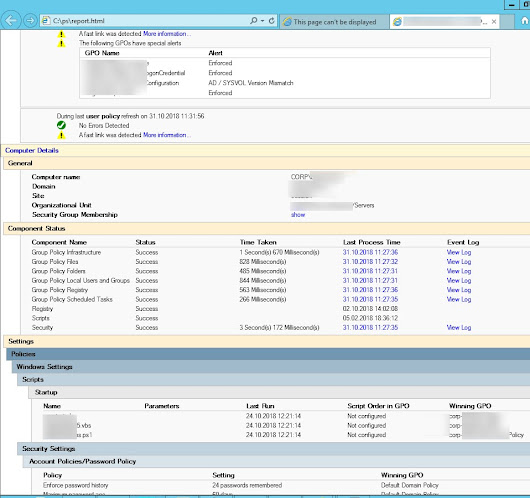
GPResult:
Group Policy Result, is the result of all policies applied to the machine.
GPresult displays the result of all policies applied on the device, both for the user and computer.
You should run GPResult if you want to understand what group policies are applied to the machine.
gpresult /v >> c:\gpresult.txt
Simple output text file
GPResult /h c:\PS\gpo-report.html /f














No comments:
Post a Comment