A vulnerability
Is a weakness in an IT system (OS or Application)
that can be exploited by an attacker to deliver a successful attack.
An exploit
Is a program, or piece of code, designed to find
and take advantage of a security flaw or vulnerability in an application or
computer system, typically for malicious purposes such as installing malware.
An exploit is not malware itself, but rather it is
a method used by cybercriminals to deliver malware.
Vulnerabilities VS Anomalies
*Vulnerabilities are known attacks with known patterns that can
be matched by IPS, web application firewall (WAF) or antivirus signatures.
*Anomalies refer to unusual behavior in the network, such as higher-than-normal CPU usage or network traffic.
Anomalies must be detected and monitored (and in
some cases, blocked or mitigated) because they may be symptoms of a new attack
that has never been seen before (Zero-day attack).
Anomalies are detected through behavioral
analysis, such as DoS policies, and protocol constraint checks.
IPS
concepts
IPS protects your network from outside attacks.
IPS has two techniques to deal with these attacks:
anomaly- and signature-based defense.
Anomaly-based
defense is used when network traffic itself is used as a weapon. A host can be
flooded with far more traffic than it can handle, making the host inaccessible.
The most common example is the denial of service (DoS)
attack
The FortiGate DoS
feature will block traffic above a certain threshold from the attacker and
allow connections from other legitimate users.
* Signature-based defense
Signature-based
defense is used against known attacks or vulnerability exploits. These often
involve an attacker attempting to gain access to your network. The attacker
must communicate with the host in an attempt to gain access and this
communication will include particular commands or sequences of commands and
variables.
The IPS signatures include these command sequences,
allowing the FortiGate unit to detect and stop the attack.
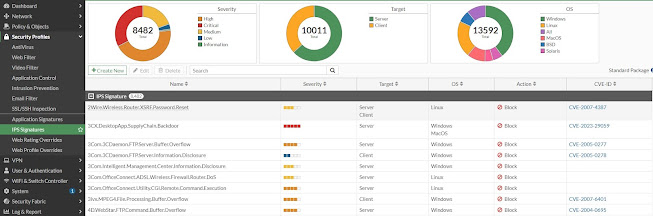
IPS components
1- IPS Signatures databases
2- Protocol Decoders
3- IPS Engines
* Application Control
* Antivirus (flow-based)
* Web filter (flow-based)
* Email filter ((flow-based)
1- Signatures
Every attack can be reduced to a particular string of commands or a sequence of commands and variables.
Signatures also include characteristics about the attack like the network protocol in which the attack will appear, the vulnerable operating system, and the vulnerable application.
To view the complete list of signatures, go to Security Profiles > IPS Signatures.
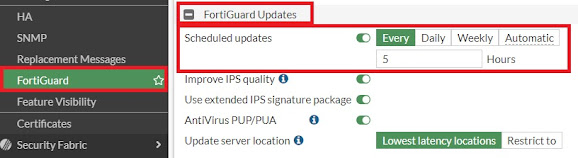
FortiGuard IPS updates
· IPS signatures updated most frequently
By default, each FortiGate firmware release includes an initial set of IPS signatures. Used to upgrade the IPS signature database. In this way, the IPS is still effective for new vulnerabilities.
· Protocol decoders are rarely updated unless the protocol specification or RFC changes (which doesn't happen often).
· The IPS engine itself changes more frequently, but still infrequently.
Types of IPS signature Databases
1- Regular signature database:
contains signatures of some common attacks that cause few or no false positives. It is a smaller database and its default action is to block detected attacks.
· contains additional signatures for attacks that have a high-performance impact, or that by their nature do not support blocking.
· In fact, due to its big size, the extended database is not suitable for FortiGate models with smaller disks or memory. However, for high security networks, you may need to enable the extended signature database.
· the extended database package may be disabled by default on some models, such as desktop models.
You can only enable the extended IPS database by using the CLI.
--------------------------------------------------------
To enable the
extended IPS database:
config
ips global
set
database extended
end
--------------------------------------------------------
· FortiGate models with the CP9 SPU receive the IPS full extended database, and the other physical FortiGate models receive a slim version of the extended
The slim-extended DB is a smaller version of the full extended DB that contains top active IPS signatures. It is designed for customers who prefer performance.
IPS
Security Profile (IPS sensor)
From the Security Profiles > Intrusion
Prevention pane, you can create new IPS sensors
Choose signatures individually. When a signature is selected in the list, that signature is added to the sensor as a default action. You can then right click on the signature and change the action.
You can also add
rate-based signatures to block specific traffic when it exceeds a threshold for
a configured period of time.
Rate-based signatures are a subset of the signatures that are found in the database that are normally set to monitor.
This group of signatures is for vulnerabilities that are normally only considered a serious threat when the targeted connections come in multiples, a little like DoS attacks.This saves system resources and prevents repeated attacks. FortiGate does not track statistics for this client, and it is temporarily blocked.
2- By Filter
Add signatures to sensors by using filters. FortiGate adds all signatures that match the filter.
IPS Inspection Sequence
Rules are similar to
firewall policy matches; the engine first evaluates the filters and signatures
at the top of the list and applies the first match. The engine skips subsequent
filters.
Avoid doing too many filters, as this increases computation
and CPU usage.
Also, avoid making very large signature groups in each filter, which increases memory usage.
Sometimes it is
desirable to exempt specific source or destination IP addresses from specific
signatures.
This feature is very
useful during false positive virus outbreaks. You can temporarily bypass
affected endpoints until you investigate and correct the false positive issue.
IP exemptions can only be configured on a single signature. Each signature can have multiple IP exemptions.
IPS Actions
· Allow: to allow traffic to continue to the destination.
· Monitor: to allow traffic to continue to its destination and log the activity.
· Block: to silently drop traffic that matches any of the signatures contained in the entry.
· Reset: if selected, a TCP RST message will be generated when the signature is triggered.
· Default: to adopt the default action of the signature.
· Quarantine: allows you to isolate an attacker's IP address for a specified period of time. You can set the quarantine duration to any number of days, hours, or minutes.
If enabled, FortiGate
saves a copy of packets that match the signature.
What is DDoS attack?
In DDoS attacks, an attacker directs a large number of computers to attempt normal access of the target system.
If enough access attempts are made, the target is overwhelmed and unable to service genuine users.
The attacker does not gain access to the target system, but it is not accessible to anyone else.
Besides protecting against threats and exploitation of vulnerabilities, the IPS engine is also responsible for mitigating DDoS attacks using anomaly-based defense
Since the botnet
database is part of the FortiGuard IPS contract, administrators can enable
scanning for botnet connections to maximize its internal security.
{A botnet refers to a group of computers which have been infected by malware and have come under the control of a malicious actor.
The term botnet is from the word’s robot and network and each infected device is called a bot.}
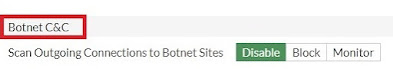
·
Disabled:
do not scan connections to botnet servers
·
Block:
Block the connection with the botnet server
·
Monitoring:
record the log of connecting to the botnet server
Best Practices
1- Before implementing an IPS, you need to analyze your network needs.
• Enabling the default profile across all policies can quickly lead to problems, the fewest of which are false positives.
• Performing unnecessary inspections on all network traffic can result in high resource utilization, which can hinder FortiGate's ability to handle regular traffic.
2- You must assess the applicable threats. If your organization only runs Windows, you don't need to scan for Mac OS vulnerabilities.
3- It is also important to consider the direction of traffic. There are many IPS signatures that only apply to clients, and many signatures that only apply to servers.
4- Create IPS sensors specific to the resources you wish to protect. This ensures that FortiGate does not scan insignificantly signed traffic.
5- IPS is not a fixed implementation. You need to monitor the logs regularly to find unusual traffic patterns and adjust the configuration of the IPS profile according to the actual situation. You should also regularly audit your internal resources to determine if certain vulnerabilities still apply to your organization.
6- Certain vulnerabilities apply only to encrypted connections. In some of these cases, FortiGate cannot reliably identify threats without being able to parse the payload. For this reason, if you want to get the most out of your IPS and WAF capabilities, you must use SSL inspection profiles.
7- Usually, the traffic that needs to be inspected, such as anti-virus and IPS, is processed by the CPU on the FortiGate. However, there are dedicated chips on certain FortiGate models that offload these inspection tasks. This frees up CPU cycles to manage other tasks, and also speeds up sessions that require security checks.
Troubleshooting
2- You should periodically check for the most recent update timestamp.
3- The high CPU usage of the IPS engine is abnormal and needs to be checked. You can troubleshoot these issues by using CLI, {diagnose test application ipsmonitor} command
· Option 5:
enables IPS bypass mode. In this mode, the IPS engine is still running, but no
traffic inspection is performed.
If
CPU usage drops after this, it usually indicates that the
traffic being inspected is too high for that FortiGate model.
If
CPU usage remains high after enabling IPS bypass
mode, it usually indicates a problem with the IPS engine and needs to be
reported to Fortinet Support.
·
Option 99: ensures
that all IPS-related processes restart gracefully.
When there is no enough memory in the IPS socket buffer to accommodate new packets, IPS will enter fail open mode.
What happens in this state depends on the IPS configuration.
·
If the
fail-open setting is enabled, some new packets (depending on system load) will
pass through without being inspected.
·
If this
setting is disabled, new packets will be dropped.
Frequent IPS failures to open events usually indicate that the IPS cannot meet the traffic requirements. So, try to recognize patterns {Has traffic increased recently? Has throughput demand increased? Are fail-opens triggered at specific times of the day?}.














No comments:
Post a Comment