What
is Active Directory?
Active
Directory (AD) is a directory service that runs on Microsoft Windows Server.
The
main function of Active Directory is to enable administrators to manage
permissions and control access to network resources.
In
Active Directory, data is stored as objects, which include users, groups,
applications, and devices, and these objects are categorized according to their
name and attributes.
Active
Directory Services
Active
Directory Domain Services (ADDS):
are the core component of Active Directory and provide the primary mechanism
for authenticating and access authorization.
Lightweight
Directory Services (LDAP)
Certificate
Services (CS)
Active
Directory Federation Services (ADFS)
1- Logical
· Object
· Organizational Units &containers (not possible to link a Group Policy Object (GPO) to a container)
·
Domains
·
Trees
· Forests
2- Physical
·
Domain Controllers
·
Sites
·
Replication Within a Site
|
PARAMETER |
LDAP |
AD |
|
Abbreviation |
Lightweight Directory
Access Protocol |
Active Directory |
|
Philosophy |
An application protocol
for querying and modifying items in directory service providers like Active
Directory, which supports a form of LDAP. |
Active Directory is a
database-based system that provides authentication, directory, policy, and
other services in a Windows environment. It is a centralized hierarchical
directory database which contains information of all user accounts in the
network. |
|
Functionality |
LDAP is one of the
protocols you can use to communicate with Active directory |
AD is a directory
services database |
|
Standard |
LDAP is a standard |
AD is Microsoft's
proprietary |
AD
VS DC
AD:
Identity and access management directory services.
DC:
Hardware Server that hold and manage AD.
Active
directory database uses the “Extensible Storage Engine (ESE)” which is
an indexed and sequential access method (ISAM) database.
It
is uses record-oriented database architecture which provides extremely fast
access to records. ESE indexes the data in the database file. This database
file can grow up to 16 terabyte and hold over 2 billion records.
·
Ntds.dit: active directory database file, where
all the active directory data stored.
·
Edb.log: transaction log files to store the
directory transaction before write in to the database file, each of them is
10mb or less in size.
·
Edb.chk: file to keep track of data transaction
committed into database from log files (Edb*.log).
·
Temp.edb: This is used during the active directory
database maintenance to hold data and also to store info about large
in-progress AD data transactions.
·
Res1.log and Res2.log: Even we can’t see it in
this example this is a file type which will store log entries if edb.log file
full.
SYSVOL:
The
SYSVOL folder is a shared on an NTFS volume on all the domain controllers
within a particular domain.
SYSVOL
is used to deliver the policy and logon scripts to domain members.
By
default, SYSVOL includes 2 folders:
·
Policies
Default
location:
%SystemRoot%\SYSVOL\SYSVOL\<domain_name>\Policies
·
Scripts
Default
location:
%SystemRoot%\SYSVOL\SYSVOL\<domain_name>\scripts
Note: These default locations can be changed during
the DC setup.
**************************************************************************************************
How to check Active Directory Health
1- Microsoft Best Practices Analyzer (BPA)
BPA is
a server management tool that is available in Windows Server® 2008 R2.
BPA
can help administrators reduce best practice violations by scanning one or more
roles that are installed on Windows Server (2008 R2 or Later), and reporting
best practice violations to the administrator.
If you have a problem in configuration You will get Errors or Warning. for each you can find a short description and a link for how to fix.
2- DCDiag tool
Microsoft
command-line utility that can be used to check the health of Active Directory
domain controllers.
It is also used to diagnose DNS servers, AD replication, and other critical domain services within your Active Directory infrastructure.
To
check ADDS Run
these commands in the PowerShell console
dcdiag
/e /v /q
Dcdiag /e | select-string -pattern '\. (.*) \b(passed|failed)\b test (.*)'
/a Tests all the servers on this site.
/e Tests all the servers in the enterprise.
Overrides /a.
/v Verbose. Prints extended information.
Q
Quiet. Prints only error messages.
To
check DNS run
these commands in the PowerShell console
DCDiag
/Test:DNS /e /v
To fix DNS issues run these commands in the PowerShell console
(Replace
dc01.test.com with DC FQDN)
DCDiag
/Test:DNS /e /v /s:dc01.test.com /fix
Then
on all domain controllers
run the command:
ipconfig
/registerdns
dcdiag
/test:netlogons

3- Make sure that all the dependency services are running properly.
There
are four system components that are critical for the efficient running of
Active Directory Domain Services:
1) DFS
Replication, 2) DNS Server, 3) Intersite Messaging, and 4) Kerberos Key
Distribution Center.
Run these commands in the PowerShell console
$Services='DNS','DFS Replication','Intersite Messaging','Kerberos Key Distribution Center','NetLogon',’Active Directory Domain Services’
ForEach ($Service in $Services) {Get-Service $Service | Select-Object Name, Status}
Get-Service -name ntds,adws,dns,dnscache,kdc,w32time,netlogon,DFSR,IsmServ
Repadmin
is a replication diagnostic tool.
run
these commands in the PowerShell console
repadmin
/replsum

To
Show more details on replication
run these commands in the PowerShell console
repadmin
/showrepl

To force synchronization run
these commands in the PowerShell console
Repadmin
/syncall
To view the replication queue:
Repadmin /queue
5- Detect unsecure LDAP binds:
The
first step towards mitigating the vulnerability of unsecure LDAP binds is to
identify whether you are affected, which you can do by looking through event ID
2887. Event 2887 is logged by default in the DC once every 24 hours, and it
shows the number of unsigned and cleartext binds to the DC. Any number greater
than zero indicates your DC is allowing unsecure LDAP binds.
run
these commands in the PowerShell console.
Get-WinEvent
-FilterHashtable @{
LogName = 'Security'
ID = 2887
}
Get-WinEvent
-FilterHashtable @{
LogName = 'Security'
ID = 4719
}
6- Active Directory Events to Monitor
Monitoring the directory service is essential for preventing cyber-attacks and delivering the best end-user experience to your users.
Below a list of the most important network events that you should look out for. If you see any of these events then you should investigate further ASAP to make sure that your service hasn’t been compromised.
4618 - A security event pattern has been recognized.
4649 - A replay attack was detected (potentially a false positive).
4719 - A system audit policy was changed.
4765 - SID History added to an account.
4766 - The attempt failed to add SID History to account.
4794 - Attempt to launch Directory Services Restore Mode.
4897 - Role separation enabled.
4964 - Special groups have been assigned a new logon.
5124 - Security updated on OCSP Responder Service.
1102 - Audit log was cleared.
W32tm.exe
tool used to configure Windows Time service (W32time) settings. You can also use
W32tm.exe to diagnose problems with the time service.
Why
time is important?
When
a Windows server receives a Kerberos authentication request, it compares the
timestamp in the request to its local time. If the difference between the local
time and the timestamp is too big (within 5 minutes of each other – default
setting), the authentication request is rejected and Kerberos authentication
fails and users won’t be able to login.
*Besides that, the use of the correct time is also important for AD’s multi-master replication model used between all DCs, were timestamps are used to resolve AD replication conflicts.
To
monitor run these commands in the PowerShell console
w32tm
/monitor
The
Get-ADHealth.ps1 PowerShell script will check the health of your AD environment and provide you with a report that you can use to identify and
resolve any issues:
· Server
· Site
·
OS Version
·
Operation Master Roles
·
DNS
·
Ping
·
Uptime (hrs)
·
DIT Free Space (%)
·
OS Free Space (%)
·
DNS Service
·
NTDS Service
·
NetLogon Service
·
DCDIAG: Advertising
·
DCDIAG: Replications
·
DCDIAG: FSMO KnowsOfRoleHolders
·
DCDIAG: FSMO Check
·
DCDIAG: Services
·
Processing Time
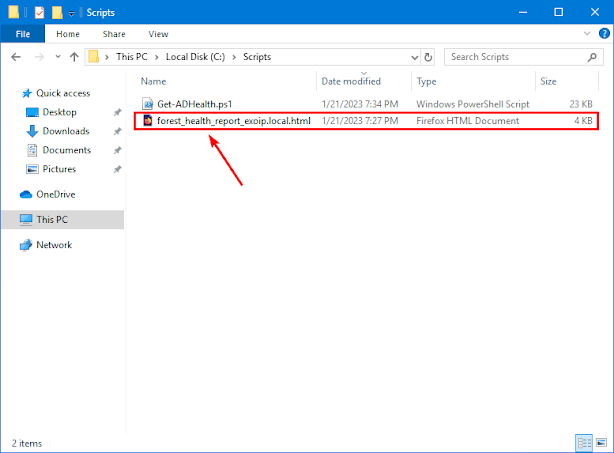
Download and place Get-ADHealth.ps1 PowerShell script on the Domain Controller C:\scripts folder. If you don’t have a scripts folder, create one.
Create
Active Directory health report
To
generate an Active Directory health report, go through the below steps:
1- Sign in to
a Domain Controller
2- Run
PowerShell as administrator
3- Change
directory path to C:\scripts
4- Run
.\Get-ADHealth.ps1 -ReportFile
PS C:\> cd C:\scripts
PS C:\scripts> .\Get-ADHealth.ps1 -ReportFile
This
is how it looks in our example.
















No comments:
Post a Comment