High Availability System (HA):
Is the ability of overall system resilient to failure by keeping systems running through outages and failures, or at least minimizing the impact of those outages.
Only a very small amount of downtime is acceptable, e.g., 0.05 % (= 99.95 % uptime), for a system to be considered highly available.
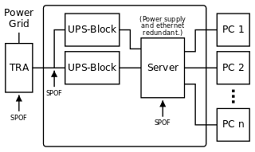
SPOF Is a component whose failure will cause the
entire system to fail.
A single disk, whose failure would bring down a system, is a SPOF.
Computer systems without clustering represent a
SPOF.
A single data center without a DR site is a SPOF.
Ultimately, of course, the Earth is a SPOF.
Fault Tolerance System (FT):
FT is the ability of the system to continue operating even in the event of a failure.
By making individual components of a system resilient to failure.
No downtime is acceptable for a system component to be considered fault tolerant.
Backup Strategies
What is backup?
Backup is the process of creating a copy of the data on your system that you use for recovery in case your original data is lost or corrupted.
1- The 3-2-1 backup strategy
2X local copies (on-site) but on different storage types.
1X copy off-site.
The 3-2-1-1-0 backup strategy
2X local copies (on-site) but on different storage types.
1X copy off-site.
1X copy offline, air-gapped or immutable (No Access).
0X errors with Sure Backup recovery verification
The 4-3-2 backup strategy
3X copies of your Data in three locations (one on-prem with you, one with an MSP like Continuity Centers, and one stored with a cloud provider).
2X copy off-site granting higher data protection against disasters and targeted attacks.
Which Backup Strategy Is Right for You?
First, any backup strategy is better than no backup strategy. As long as it meets the core principles of 3-2-1 backup, you can still get your data back in the event of a natural disaster, a lost laptop, or an accidental deletion. To summarize, that means:
3-2-1-1-0 or 4-3-2, giving your data an additional layer of protection by virtually isolating it so it can’t be deleted or encrypted.

















No comments:
Post a Comment